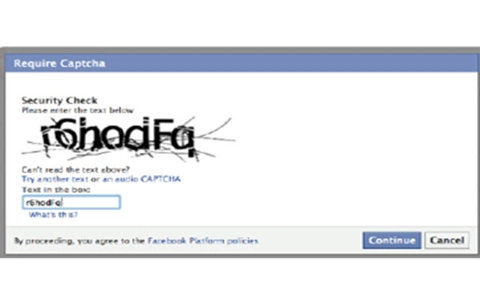
Cyber Security Threats
The lesson covers, security measures including CAPTCHA, Biometric security measures and Password systems as well as automatic software updates.
Additional details
| Year band(s) | 9-10 |
|---|---|
| Content type | Lesson ideas |
| Format | Document |
| Core and overarching concepts | Privacy and security, Digital systems |
| Australian Curriculum Digital Technologies code(s) |
AC9TDI10P01
Develop techniques to acquire, store and validate data from a range of sources using software, including spreadsheets and databases
AC9TDI10P14
Apply the Australian Privacy Principles to critique and manage the digital footprint that existing systems and student solutions collect |
| Keywords | Cyber Security, Security threats, CAPTCHA, Password systems, Biometric measures |
| Organisation | Cyber Security Challenge UK |
| Copyright | 2017 Cyber Security Challenge UK. May be subject to Copyright Act statutory licence. |
Related resources
-

eSafety Commissioner: Video and resource library
Online safety resources for secondary schools supported by lesson plans and multimedia resources. Use the filters to find tailored resources suitable for your classroom needs.
-
NovaLab: Cyber security
These cyber security short animated videos each have a quick quiz to complete. The videos cover a basic intro into cyber security, hacking and privacy, cyber codes and there is a game too for students to apply their understandings.
-

Creating a Biology AR poster using Unity
In this lesson, students explore how to design and implement a simple Augmented Reality (AR) world to project DNA model using Unity 3D and Vuforia SDK for Unity 3D.
-

Human Anatomy with Virtuali-tee
In this learning activity, students explore human organ systems using Virtuali-tee.
-

Experience ‘Okavango Delta’ in Southern Africa with VR
In this lesson, students will virtually explore one of the wonders of nature called ‘Okavango Delta’ using immersive VR technology.
-

Filter bubbles, bias, rabbit holes and nudging
This lesson focuses on the AI systems that recommend content in various applications that students use on a day-to-day basis. It draws on students’ ethical understandings during analysis of these systems.
-
Working together
In this lesson sequence students, through role-play and other activities, develop understandings of the role of hardware and software in managing, controlling and securing the movement of and access to data in networked digital systems.
-

The shock of the new
Using four inventions from 1985, this lesson sequence explores the impact of innovation, supporting circumstances, how individuals contribute to change and the importance of addressing benefits as well as risks in the development of new systems.